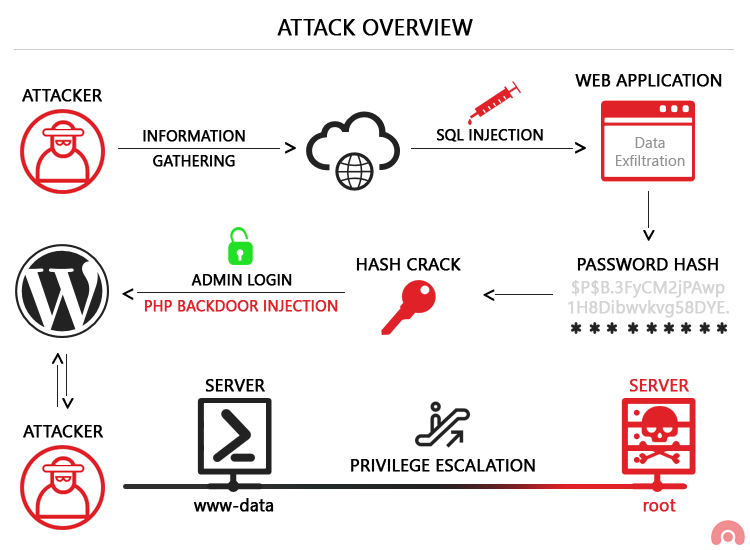
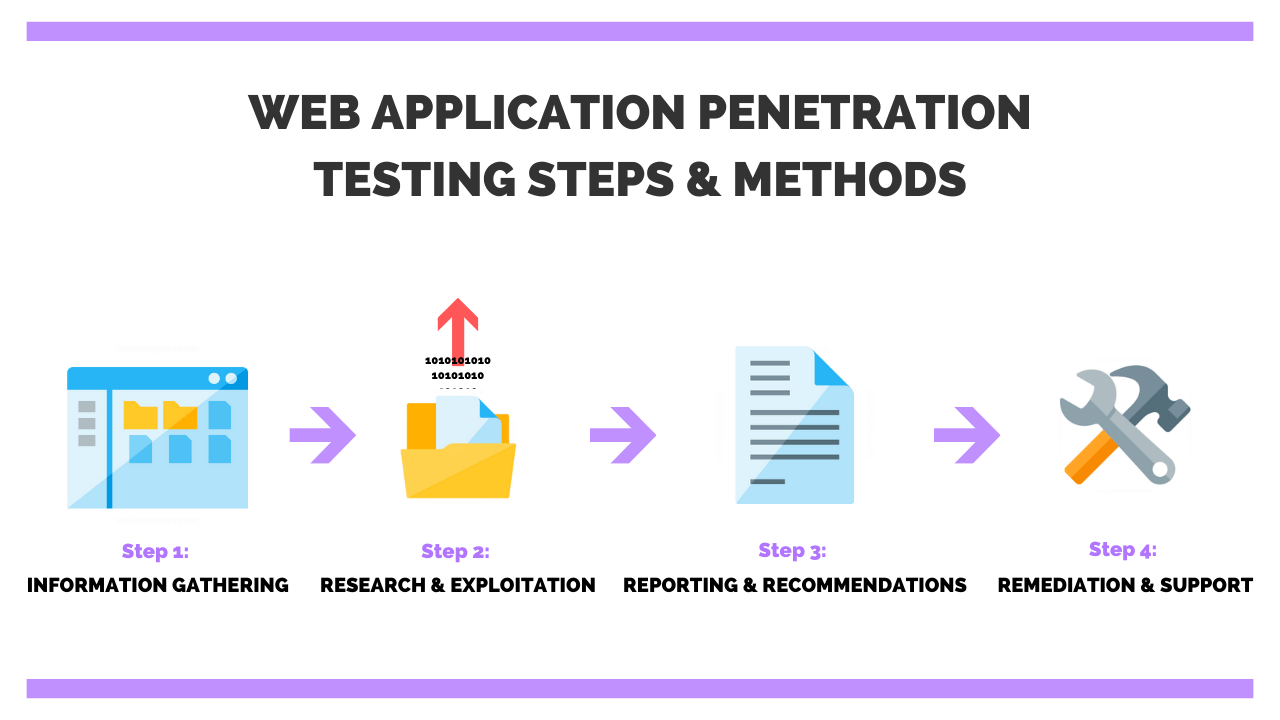
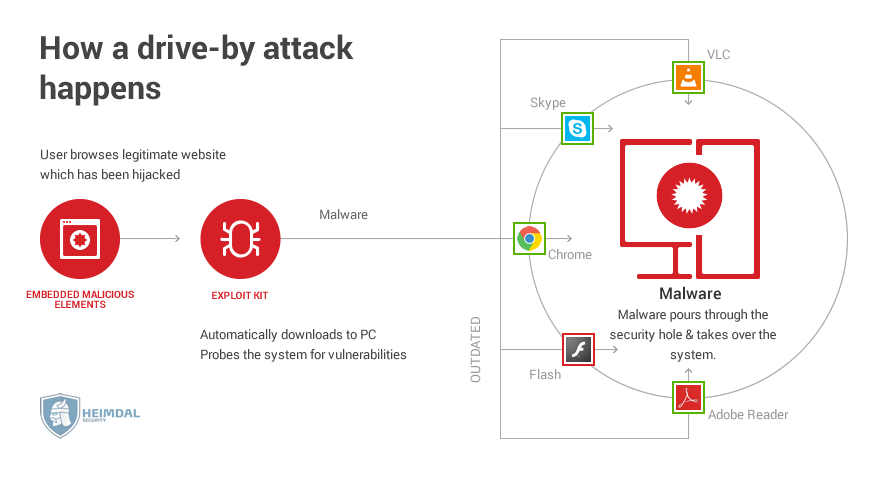
15 Vulnerable Sites To Legally Practice Your Hacking Skills Checkmarx Application Security
www.checkmarx.com

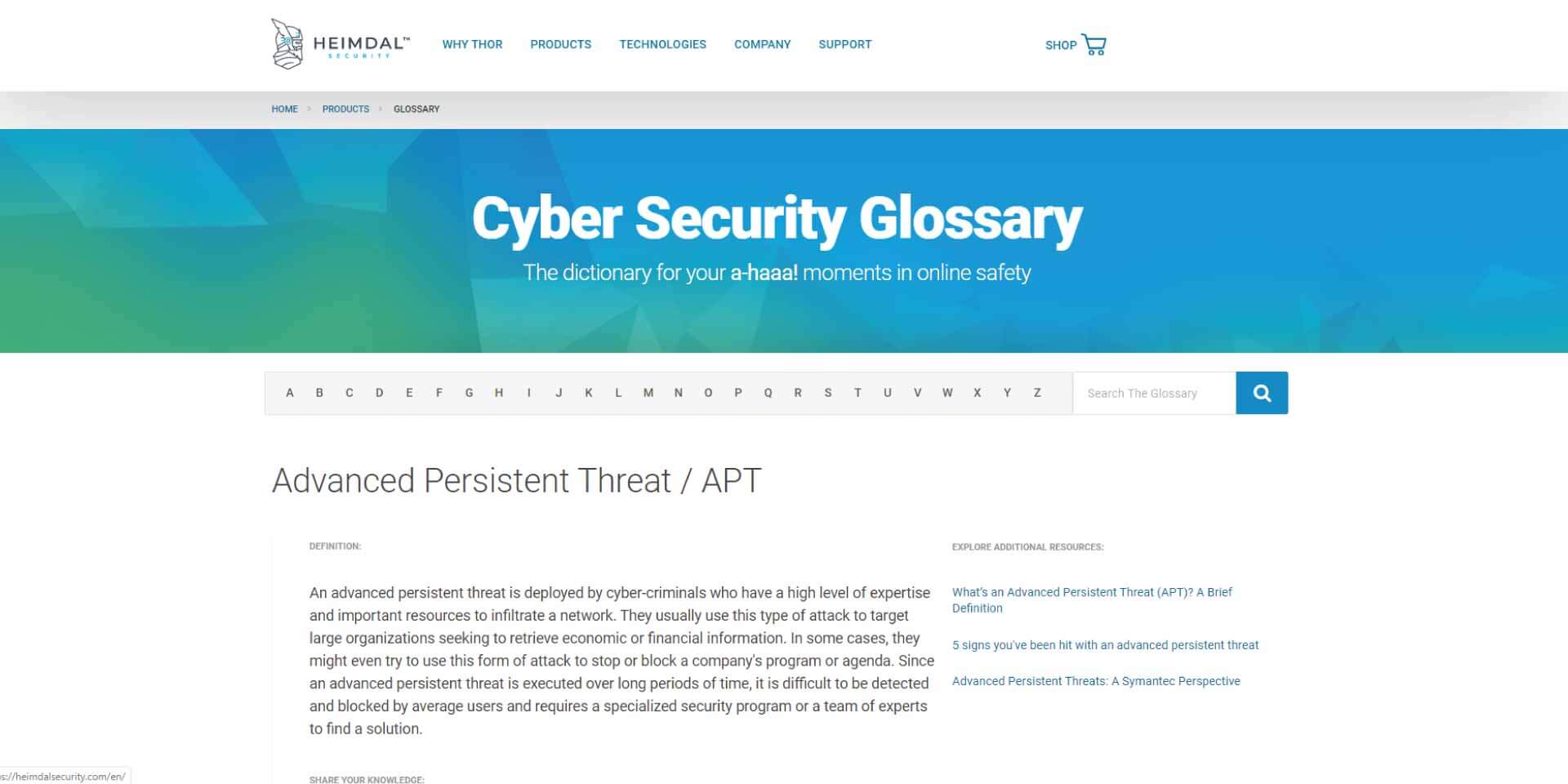
The 11 Best Cyber Security Books Recommendations From The Experts Hashed Out By The Ssl Store
www.thesslstore.com
You can download a free 30 day trial copy from vmware.

Cyber security web application exploitation free download. See screenshots read the latest customer reviews and compare ratings for cyber security tutorial free. Awae is designed for. Free download latest version from here.
Download this app from microsoft store for windows 10 mobile windows phone 81 windows phone 8. Cyber security tools are important utilities which help to manage and protect network security with ease. Explain the impact of exploitation of web application flaws.
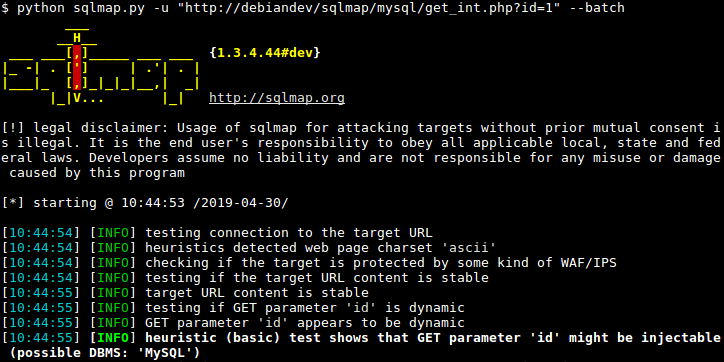
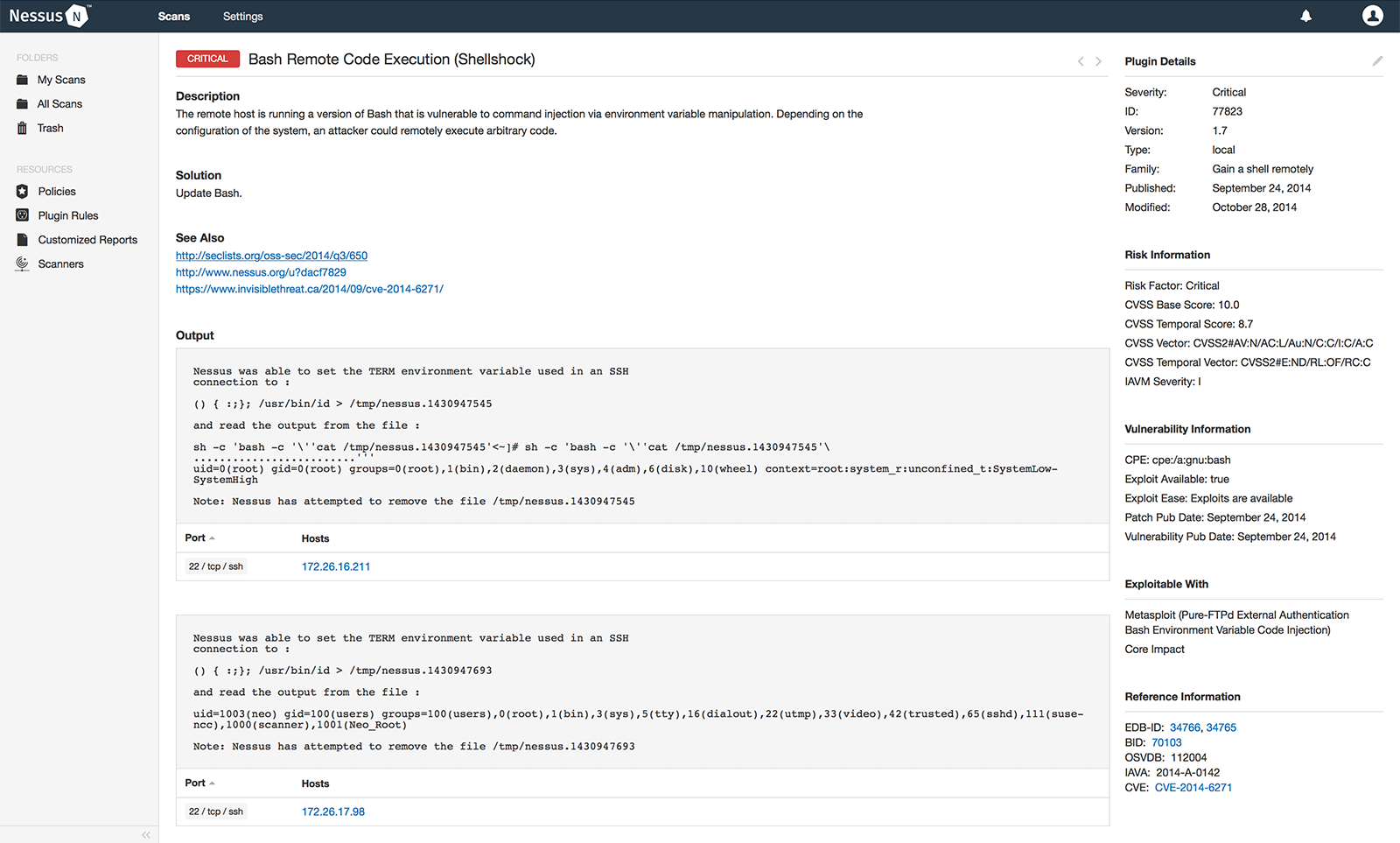
Beef is short for the browser exploitation framework. Cyber security web application exploitation download. Experienced penetration testers who want to better understand white box web app pentesting.
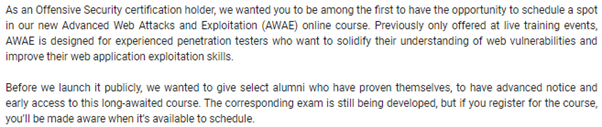
Advanced web attacks and exploitation is not an entry level course. Amid growing concerns about web borne attacks against clients including mobile clients beef allows the professional penetration tester to assess the actual security posture of a target environment by using client side attack. Kali linux disc image free to download instructions provided in the course virtualbox software free to download instructions provided in the course.
Cyber security web application exploitation download. They perform advanced penetration testing and ensure protection for security of the network. Sec542 enables students to assess a web applications security posture and convincingly demonstrate the business impact should attackers exploit the discovered vulnerabilities.
Web professionals working with the codebase and security infrastructure of a web application. It is a penetration testing tool that focuses on the web browser. 0 65 2 minutes read.
Defending web applications security essentials is intended for anyone tasked with implementing managing or protecting web applications. You will find the course useful if you are supporting or creating either traditional web applications or more modern web services for a wide range of front ends like mobile applications. Sharpsbrains september 18 2020.
Web application security specialists. Anatomy of a cyber attack beginner hacking with metasploit download. Vmware will send you a time limited serial.
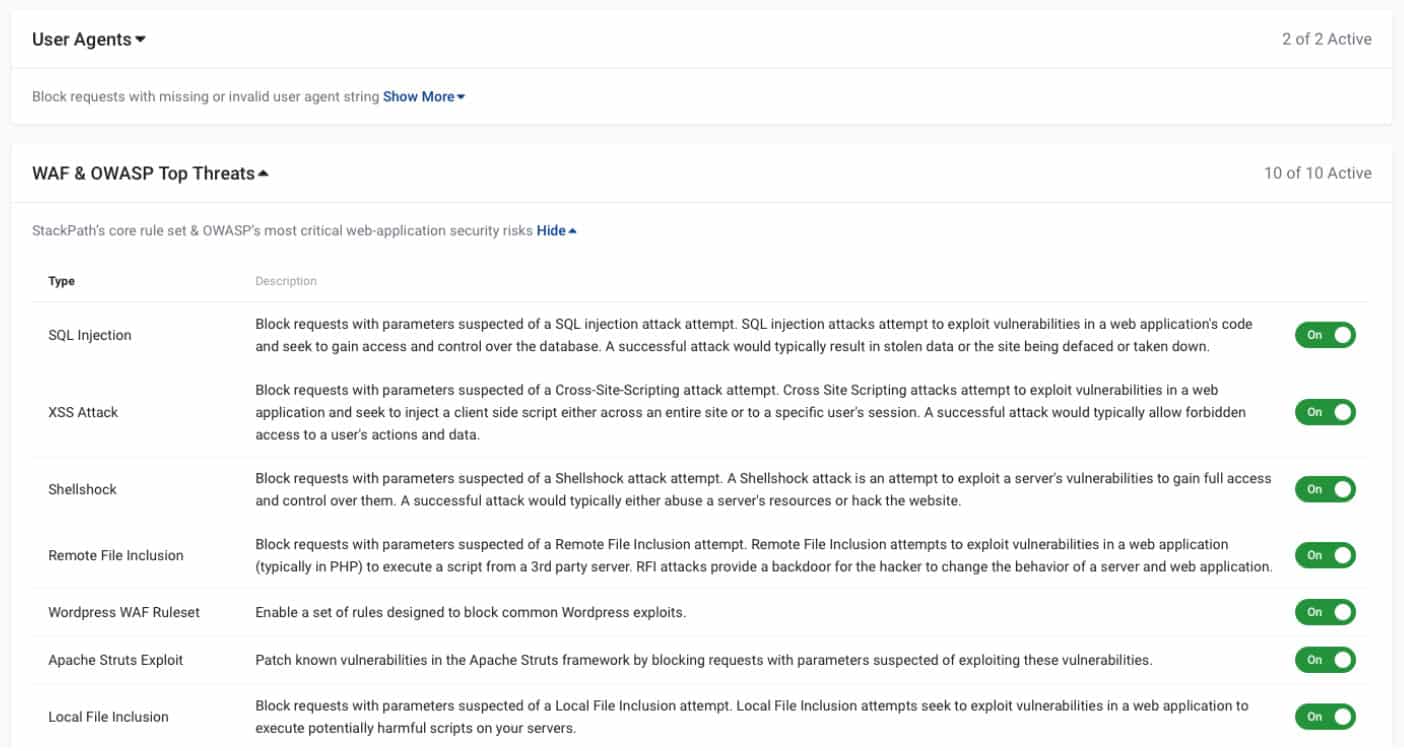
They come with powerful detection tools like spider and intruder which help to sense threats and alert the administrators.
Https Encrypted Tbn0 Gstatic Com Images Q Tbn 3aand9gcqyb9q Yl8quto4kfynsjvusul Ajxgwgur A Usqp Cau

What Is Azure Web Application Firewall On Azure Application Gateway Azure Web Application Firewall Microsoft Docs
docs.microsoft.com

Metasploit Cheat Sheet Free Download In 2020 Cheating Cheat Sheets New Tricks
www.pinterest.com

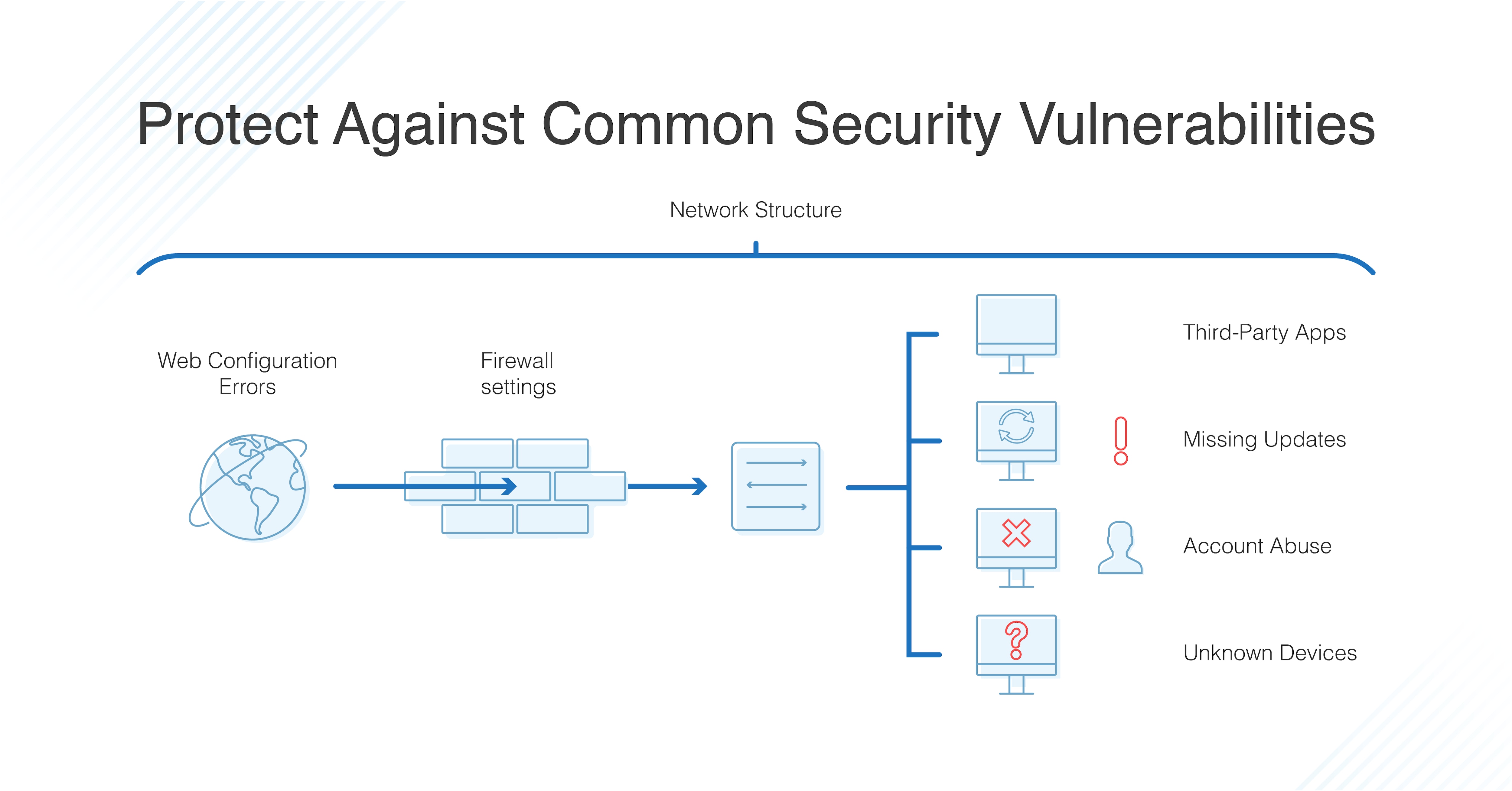
10 Types Of Application Security Testing Tools When And How To Use Them
insights.sei.cmu.edu

Cyber Security Downloading An App Don T Take That Risk Without Enough Precaution
economictimes.indiatimes.com
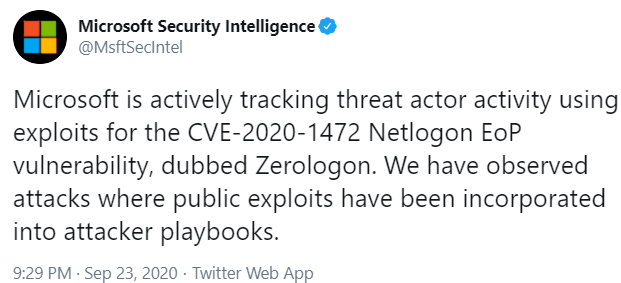
Microsoft Attackers Exploiting Zerologon Windows Flaw Krebs On Security
krebsonsecurity.com
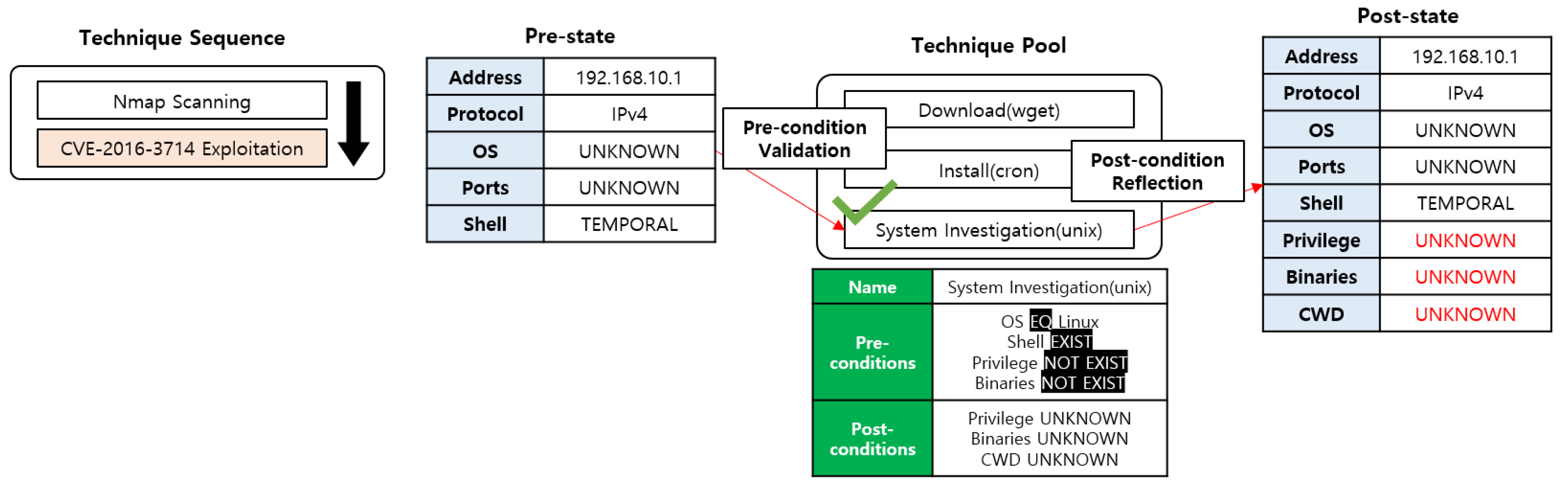
Applied Sciences Free Full Text Cyber Attack And Defense Emulation Agents Html
www.mdpi.com
Https Encrypted Tbn0 Gstatic Com Images Q Tbn 3aand9gcrizvaihhmyspbchg8fr2tpcjxz0zwg Fjtebtsg2il4 7dd2uz Usqp Cau
encrypted-tbn0.gstatic.com

Sql Injection Scanner Online Scan For Sql Injection Sqli Vulnerabilities Pentest Tools Com
pentest-tools.com

Introduction To Owasp Zap For Web Application Security Assessments Infosec Resources
resources.infosecinstitute.com

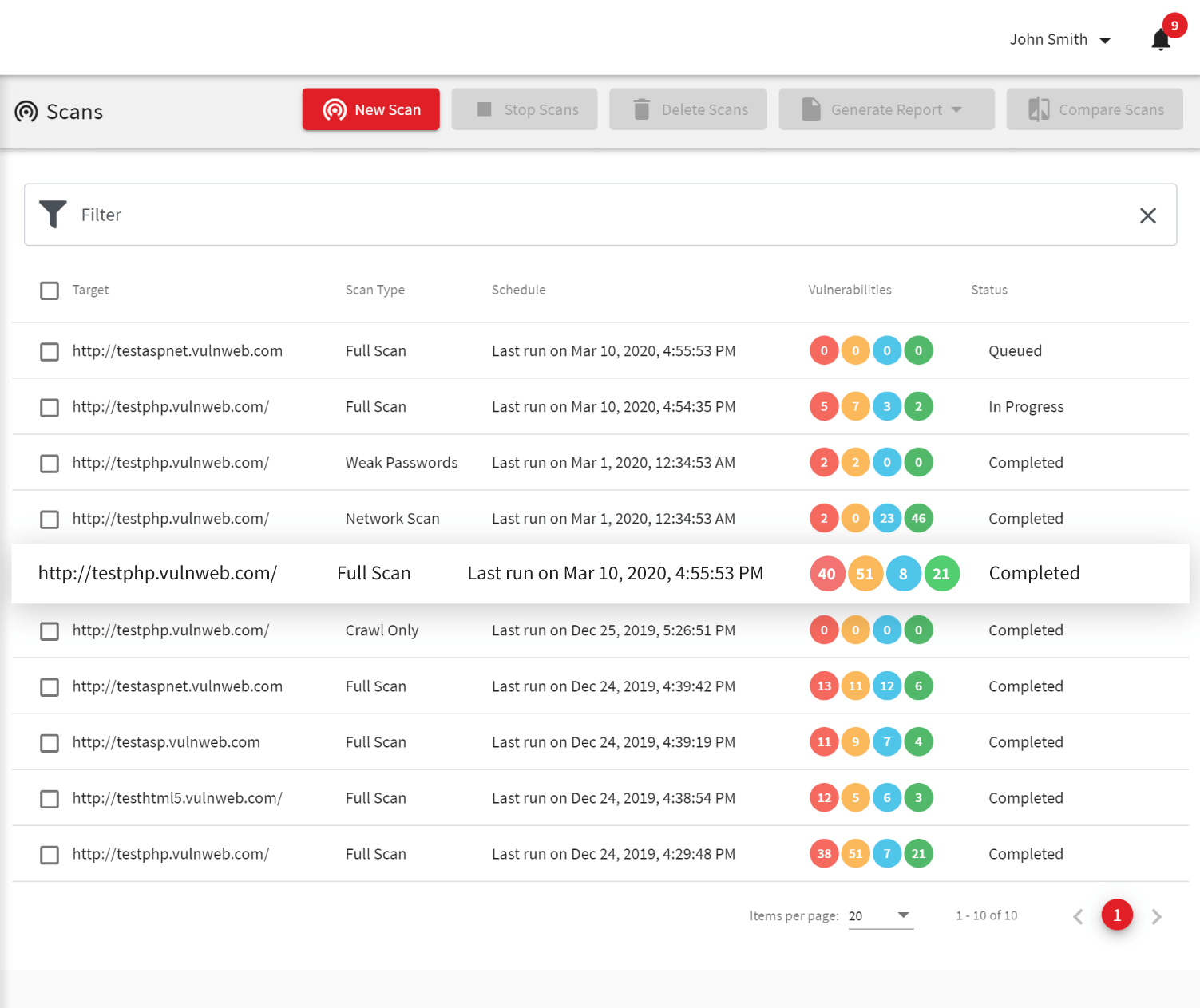
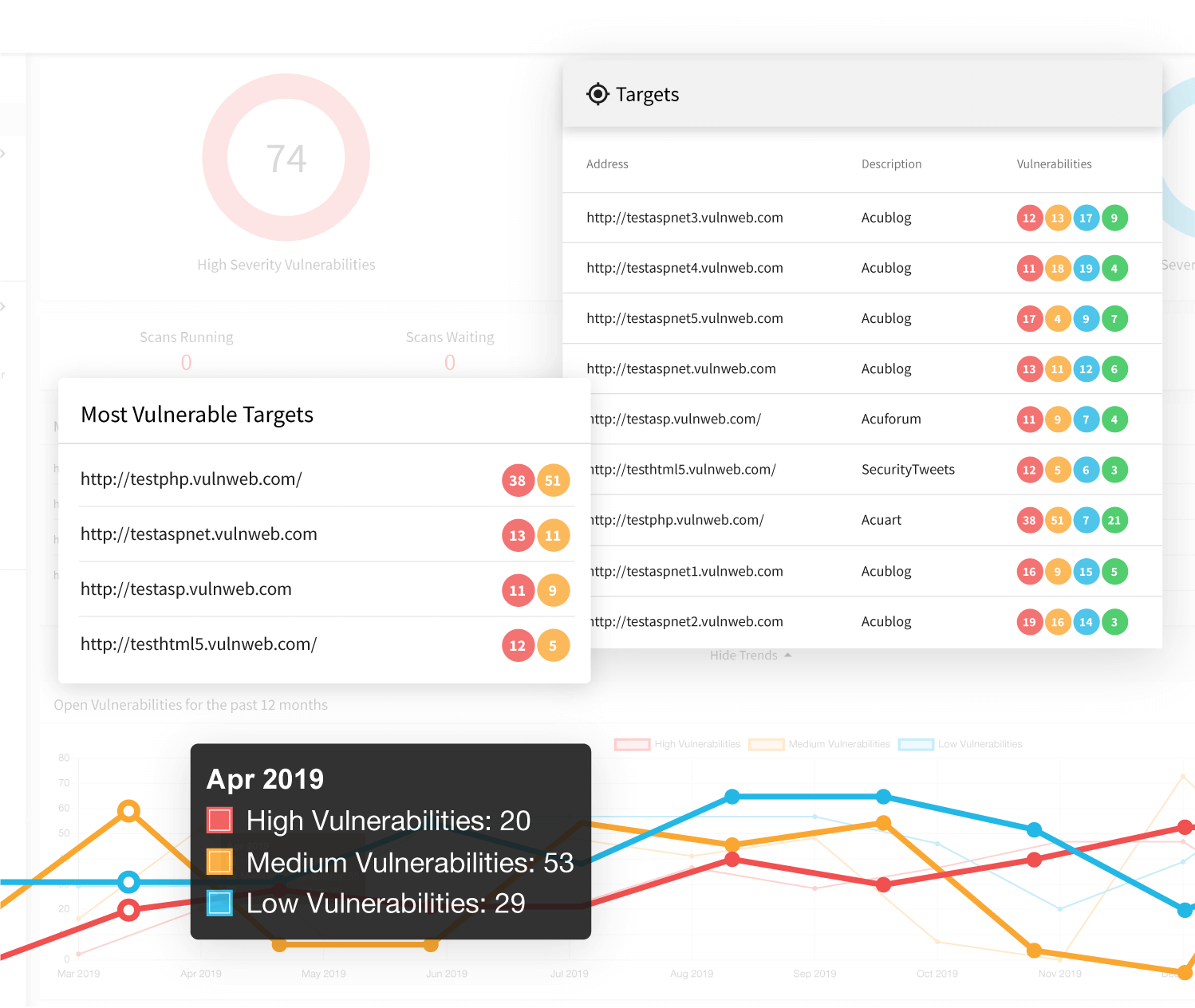
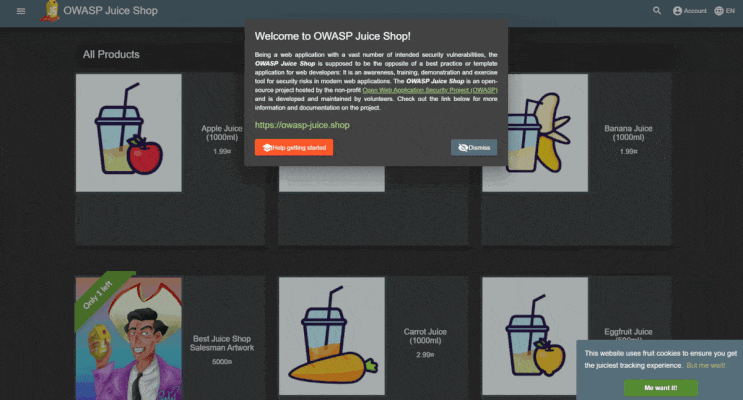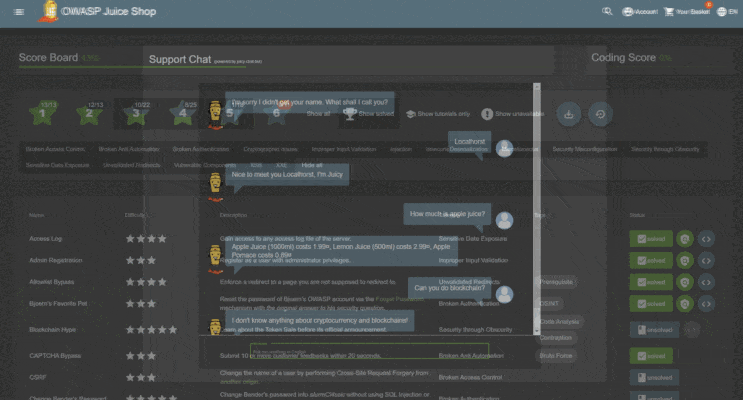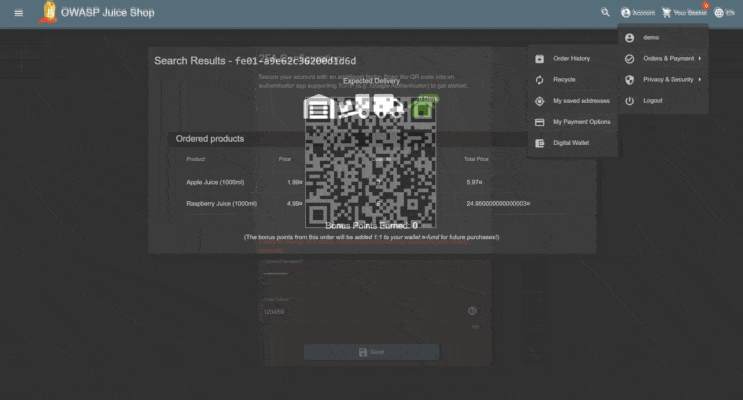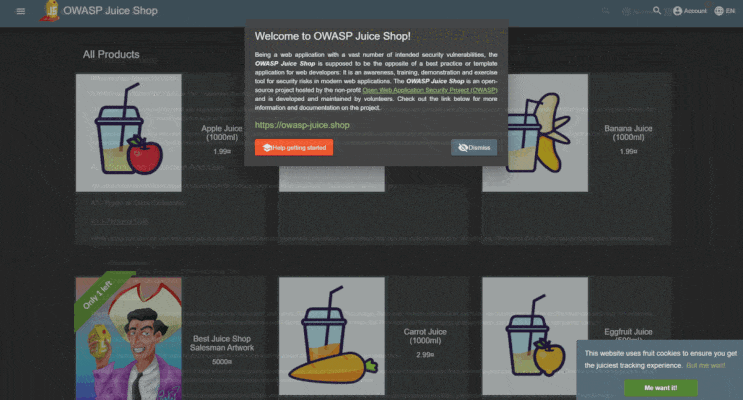
Top 5 Deliberately Vulnerable Web Applications To Practice Your Skills On Infosec Resources
resources.infosecinstitute.com
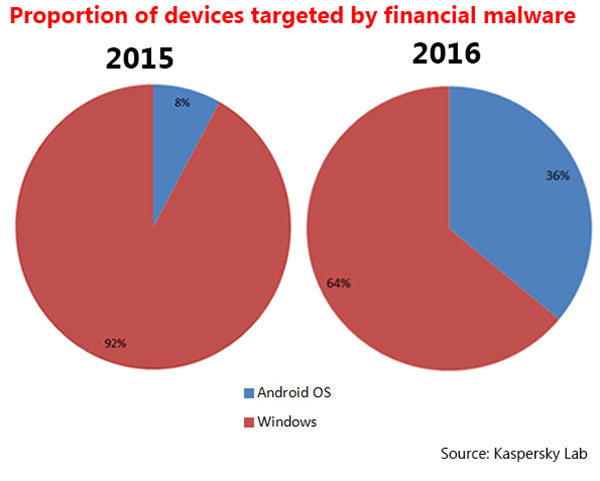
Cyber Security Downloading An App Don T Take That Risk Without Enough Precaution
economictimes.indiatimes.com

Amazon Com Web Application Security Exploitation And Countermeasures For Modern Web Applications 9781492053118 Hoffman Andrew Books
www.amazon.com
Https Encrypted Tbn0 Gstatic Com Images Q Tbn 3aand9gcqhgdvrlmqi3qlopive0cljkpoxe85nglfz 95cbyntq8pmhxbc Usqp Cau
encrypted-tbn0.gstatic.com

Owasp Top 10 Web Development Computer Security Web Application Png Clipart Circle Computer Security Computer Software
imgbin.com

Download Free Pdf Magazines And Ebooks Freeforbook In 2020 Computer Security Wireless Networking Computer Network
www.pinterest.com

Doc Lab 8 Assessment Worksheet Performing A Web Site Database Attack By Exploiting Identified Vulnerablities Milky Jimenez Academia Edu
www.academia.edu

F Secure S New Exploit Shield Zero Day Protection Help Net Security
www.helpnetsecurity.com

Kb6481 Eset Stops Wannacryptor Wannacry And Eternalblue Use Our Free Tool To Make Sure Those Windows Vulnerabilities Are Patched
support.eset.com

19 Powerful Penetration Testing Tools Best Security Testing Tools Ranks
www.softwaretestinghelp.com
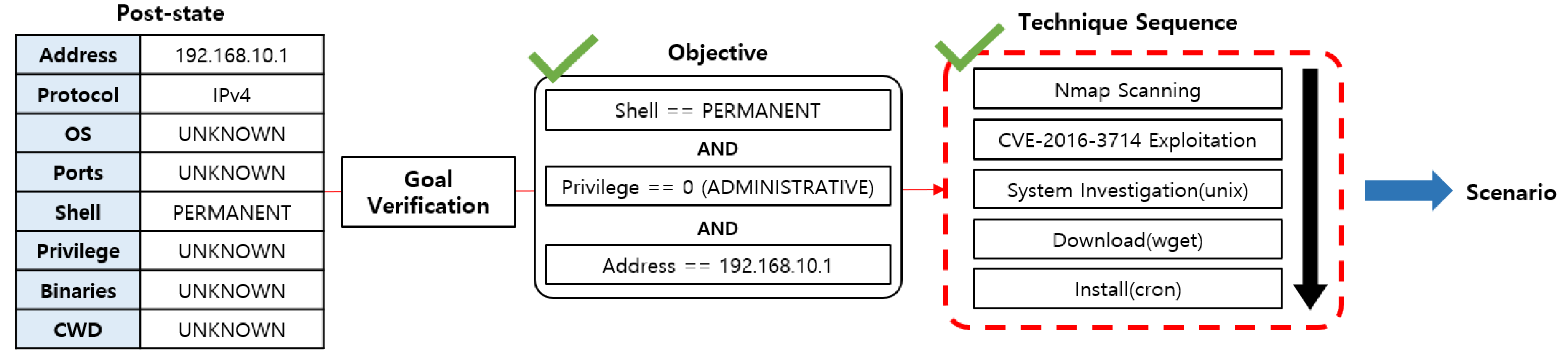
Applied Sciences Free Full Text Cyber Attack And Defense Emulation Agents Html
www.mdpi.com